Comic Transcript
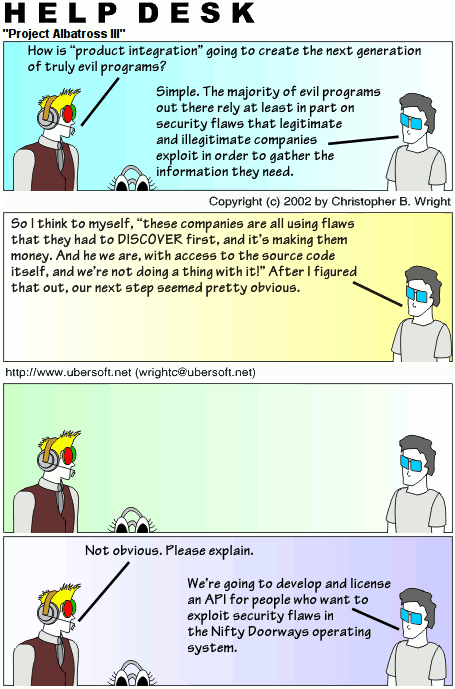
ALEX: How is “product integration” going to create the next generation of truly evil programs?
PHIL: Simple. The majority of evil programs out there rely at least in part on security flaws that legitimate and illegitimate companies exploit in order to gather the information they need.
PHIL: So I think to myself, “these companies are all using flaws that they had to DISCOVER first, and it’s making them money. And here we are, with access to the source code itself, and we’re not doing a thing with it!” After I figured that out, the next step seemed pretty obvious.
(Silence.)
ALEX: Not obvious. Please explain.
PHIL: We’re going to develop and license an API for people who want to exploit security flaws in the Nifty Doorways operating system.


